The pandemic accelerated a real change in the way people do their work. Before, employees worked in a physical office every workday. Now, they work wherever they want, however they want, and (often) what time they want. They’re also using their personal devices and corporate devices on the corporate network, on their home network, or from a hotspot at their kid’s soccer practice.
Now that we’ve transitioned to a hybrid workforce, organizations have a lot more challenges and opportunities to secure those endpoints, properly manage them, and ensure they follow company standards.
Initially, many organizations thought the hybrid work model would be temporary. But now they’re adopting this as their work lifestyle. But it’s not that simple for IT. Many of our clients are realizing that their compliance policies don’t fit hybrid work. They often lack effective policies to understand how they’re going to support these remote workers, and how they’re going to develop a Zero Trust strategy for this “new normal”.
Supporting Hybrid Work Starts with Compliance
When we talk with clients about compliance, we ask them what policies they have, how they’re enforcing them, and what they want us to configure for their environment. In response, they often ask us for best practices. Unfortunately, there are no best practices. Instead, there are recommendations based on their policies.
Though we have foundational recommendations to guide organizations to a solution, the conversation really starts with compliance. Though it’s critical to an organization’s security, it’s not a glamorous topic and is therefore often rarely discussed. (But we have a whole team that loves to talk about compliance.)
If an organization is serious about compliance, we recommend starting at the organizational level to understand what compliance policies are needed. This ensures that those who own the data understand the requirements for that data and what controls need to be in place.
Without starting at the organizational level, compliance initiatives will stall and sputter. For example, organizations will often start compliance by deploying policies like Multi-Factor Authentication. But then people will invariably ask why you’re doing it. If you’re answer to that “why” is something like, “It felt like a good idea”, it will immediately fail because there’s no policy to support it.
How to Think About Policies
At the organizational level, compliance will often start with creating policies around regulations (like HIPAA) that define what’s important to them. Next, it’s important to ask how to secure and support that regulated data. This helps organizations align their organization so that everyone understands what the data policies are, why they are important, and how they are expected to interact with the data.
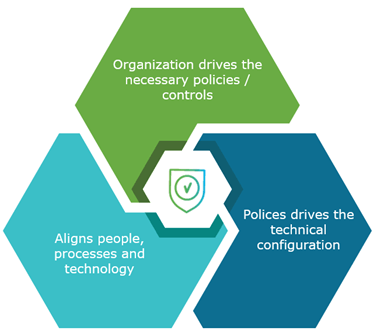
Policies also align your access and exception processes – as well as ultimately helping you align and configure your technology. So, rather than IT having to guess which features and capabilities to prioritize, organizational policies refine their focus to the most impactful technologies. Therefore, organizational policies drive the technical configuration of the environment, not the other way around. This is where many organizations struggle because they often develop the technical solution first and then later create a policy for it. It rarely works well in that situation.
Policies Guide and Integrate a Zero Trust Approach
If your organization follows the six pillars of a Zero Trust security, having an organizational policy in your environment will guide how to leverage and integrate the pillars for better interaction and effectiveness. Policies enable a comprehensive solution vs. siloed individual solutions that may or may not work. Many organizations don’t see this (or overlook it). But once they implement a good policy, everything starts fitting together.
Phase Your Approach to Compliance
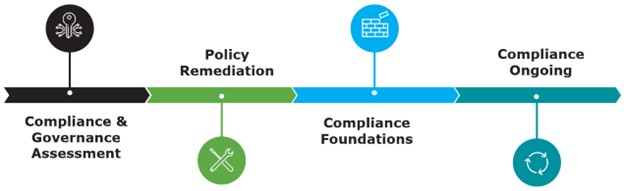
When we work with our clients, we start with a phased assessment and discuss policy remediation. Then we establish the necessary base functionality at the organization level so the IT organization can follow the appropriate policies. Throughout, it’s important to regularly meet with individual business units to understand their requirements and (if necessary) implement new technology.
Compliance and Governance Assessment
We recommend clients use a third party (like Core BTS) to do this phased assessment because it’s useful for someone from outside the organization to take a fresh look at your policies. We typically start by analyzing your current state. Then we review your current compliance policies and procedures – followed by understanding what security, technology, or methodology you’re going to use. Then we identify your risk tolerance to ensure we’re applying the right level of protection at the right places. For example, it’s wasteful to apply a million-dollar solution to a piece of data whose loss will only cost $10.

Then we provide a roadmap that shows where you are today, where you want to go, and identifies what’s in the gap between the two endpoints. This helps us provide recommendations and guidance for how we’re going to get you from point A to point B. This is referred to as a Compliance Maturity Model.
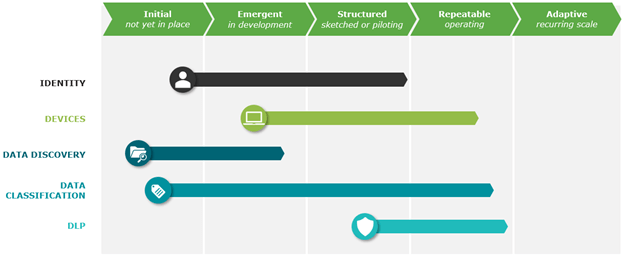
Organizational Compliance Maturity Model
The model shows where you are and where you need to be. You don’t need to be all the way on the right side of the maturity scale. It may not be part of your strategy. You may not be ready for it, or the data doesn’t need that level of security. Instead, look at the organizational level and see if your stakeholders and executives have bought into the process. This enables your team to do effective compliance with the right support.
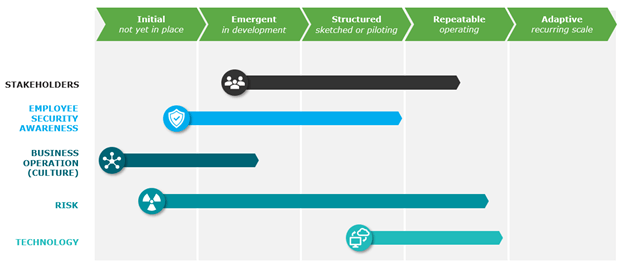
It’s important to also examine your security awareness and identify what training programs you provide.
- Do your employees understand your organizational policies?
- Do they know they’re responsible for protecting corporate data?
- Do they know they have the technology to help them prevent data accidents?
Make sure to also examine your data risk so you know how to mitigate your exposure.
Technology Compliance Maturity Model
Looking at the model from a technology perspective identifies where individual technologies fit. Don’t focus on one area and forget about the rest. Ensure you align technologies where they need to be today and to set up your organization to move to higher maturity as you grow. This is where you need to have the support policies and regulations.
Policy Remediation
Organizations typically want to immediately act on guidance and recommendations provided in their assessment. But it’s important to do things in right order.

Rather than not having a good set of policies or a set of policies that are constantly changing because you’re revising them, stop and remediate them. As part of that remediation, educate your users so they understand why you’re implementing technology changes. Doing so moves them from being potential antagonists to being supporters and adopters.
Compliance Foundation
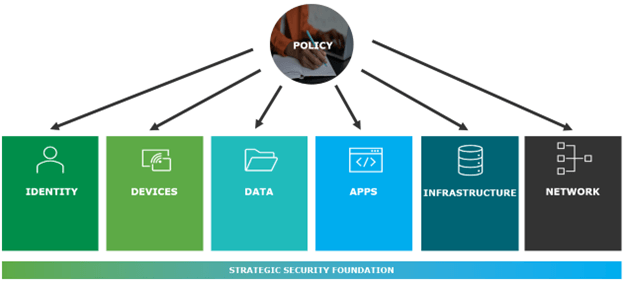
For a compliance foundation, we employ Microsoft Entra ID (formerly known as Azure Active Directory) as our policy engine because it helps us verify and ensure that our identities are healthy. We also use Microsoft Purview because it’s the framework that provides a complete set of compliance tools. Purview lets IT organization see and manage the flow of data through the IT infrastructure. It also enables device management and helps us answer questions like:
- How do we make sure a device is compliant?
- How can we allow a device to access the data environment?
- How can we enforce our policies on a device?
- How can we ensure that users can use their device to access content?
Once the foundation is established, you should help end users understand what data is or isn’t sensitive.
Continuous Compliance
Going through the compliance foundation doesn’t mean your job is done. You should routinely revisit it and conduct new assessments because regulations and technology change. Doing so will ensure your policies are still relevant and effective.
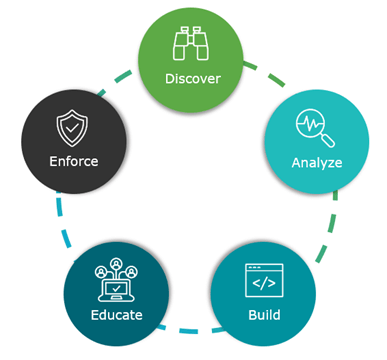
Following the continuous compliance workflow as illustrated above, you will begin with a discover phase to identify any existing policies. Then you will analyze that data to ensure you are properly implementing the policies – ruling out any false positives or missing data. And then you will build the solution. But, before you initiate enforcement, you should educate your users. Doing so will help them understand the policies, see how they enable them to do their work (not hinder it), and help them follow corporate policies to do their work the right way. Then, and only then, do you enforce policies.
The goal of this workflow is to simplify compliance so IT doesn’t worry about what policies exist and how to enforce them. They should know the controls that need to be established and have a roadmap to follow.
Compliance Assessment
If you’re thinking you need compliance but don’t know where to start, we can help. Our team loves to talk about compliance, and we created an assessment to smoothly guide you through every step of the process. To learn more, contact us today.




