Device Compliance is a journey that everyone in your organization has to go through together. Company Leadership, IT Administrators, and end users will need to cooperate to set policy, remediate issues, and enforce compliance.
Hardening Doesn’t Work Anymore
Before the modern hybrid workplace, IT often took a hardening approach to the perimeter of the corporate network by hardening the network. This approach attempted to keep devices secure when they were in the corporate network behind the company’s protective firewall. But now with many employees working out of the office, company data will have a lot more exposure to the internet. Now more than ever, IT now has to account for both on-network and off-network scenarios.
As the workplace has changed, people do their daily work using a wide variety of devices in different settings. In addition to using company-issued computers, people are also using their phones and tablets to work on-site or at home. Therefore, you need to account for different operating systems and different use cases.
Policies Mark the Beginning of Your Compliance Journey
Organizational policies make it easier for the IT team to develop and operationalize policies, educate end users about them, define device compliance standards, and enforce compliance to put your environment into a compliant and enforceable state.
This compliance journey will take several steps:
- Define Technical Standards for Device Compliance
- Survey Environment and Report Compliance Gap
- Prepare Environment for Compliance Enforcement
- Work with End Users to Remediate Gaps in Compliance Standards
- Enforce Policies to Require Compliant Devices
Defining and Enforcing Compliance
The first step is to define organizational security and compliance policies based on internal and external requirements, well known security frameworks, and industry best practices. Then decide what standards will be required, how they will be configured, and how these policies will be rolled out in your organization to operationalize the policies.
When it’s time to define your technical requirements based on pre-defined standards, common questions that will help you along include:
- Does data need to be encrypted on our endpoints?
- Do we need a specific password policy or multi-factor authentication for our workstations and mobile devices?
- Do we need specific security tools , endpoint security solutions or data protection software in-place and active all our endpoints?
For example, does your organization need to require specific data security configurations for GDPR or HIPAA requirements? Or perhaps you want to ensure you’re following the NIS or CMMC standard in addition to custom standards. Ensure you define what standards are required to allow mapping to technical specifics.
Exception Policy
Make sure an exception policy is considered because outlier devices may not be able to follow the standards you set. Perhaps some devices have legacy hardware, or software can’t be upgraded.
Therefore, make sure you define an exception process for those devices so they don’t get accidentally retired or have compliance enforced on them. Designing exception policies ahead of time will make it much smoother to review, approve / deny, and track an exception when it’s requested.
Survey and Prepare the Environment for Management and Remediation
To prepare the environment for management and remediation, make sure your devices are enrolled in the tools you selected like Microsoft Configuration Manager (on-prem), Microsoft Intune (cloud), or Microsoft-supported third-party management tools. Doing so will let you take accurate inventory close to real-time, make necessary configurations and remediations, and (most importantly) report compliance.
Make sure all endpoint devices are enrolled in appropriate endpoint management tools. This will allow for inventory to be performed, remediations to be applied, and compliance to be enforced. Microsoft Entra ID (formerly known as Azure Active Directory) Conditional Access cannot determine whether the device is in a compliant state if it’s not managed.
You may also need to enable new features and functionality within your infrastructure to manage remote device security and configuration and Microsoft Intune or through Microsoft Configuration Manager. This might include enabling Entra ID Hybrid Join, Co-Management for Configuration Manager and Intune, or setting up a Cloud Management Gateway.
When employees have their devices on-site, they need to be able to talk to internal servers and management tools. When they’re working remotely, users will need to have the infrastructure in place to have those devices connect to management tools for policy configuration and enforcement. This might include endpoint management tools like Configuration Manager as well as antivirus tools that are centrally managed.
Use your existing tools to survey your environment and report any compliance gaps. Since many people took their work computers home during the pandemic (and may still work from home), they may not have had all the tools or policies set on their computers before they left. You need to ensure that all devices have tools installed that report back to your systems, and let you survey them to ensure they’re compliant.
Configure Integration
In the integration stage, we recommend implementing co-management with Intune and Configuration Manager. It enrolls the devices in both Intune and Configuration Manager so they can be simultaneously managed in the cloud and on-prem. To keep configured manager devices connected when they’re away from the corporate network, it’s useful to use a cloud management gateway with the Microsoft Cloud.
Configuring conditional access policies is what ties everything together. It lets you set if-this-then-that scenarios for devices like checking if a device is compliant and then automatically denying access to non-compliant devices.
Implementing Compliance Policies on Different Devices
Different device types have different capabilities and will require specific encryption to bring them into compliance.
iOS / iPadOS Compliance Policy (Example)
This is a possible iOS compliance policy you can set for iPad and iOS iPadOS devices:
- Block jailbroken devices
- Require that a minimum iOS version is installed
- Require a 6-digit numeric passcode
- Require passcode 5 minutes after screen lock
- Lock screen after 5 minutes of inactivity
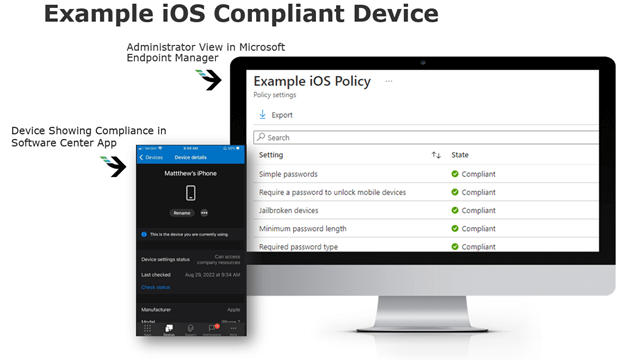
iOS Compliant Device (Example)
If you implemented the compliance policies above, the image below shows what the end user would see on their device and what the administrator would see in the Intune console. Administrators can see a detailed list of applied compliance checks and if the device passes. On the device using the software center app, the end user can see they are able to access corporate resources – meaning their device passed the checks and is in a compliant state.
Windows 10 Compliance Policy (Example)
To maintain your cybersecurity posture, built-in Windows compliance checks will validate out-of-the-box that endpoint security solutions are in place, including requiring minimum patch versions, encryption configured, Firewall enabled, TPM present, and that antivirus is installed.
To help contain malware, built-in compliance checks can verify that your endpoint protection and antivirus software is installed and active. One great feature is that the anti-malware doesn’t have to be Windows Defender; it can be any third-party antivirus tool that integrates with Windows 10’s Security Center.
You can also require that it meets the password compliance complexity requirements for Azure AD devices that are not joined to a domain. We see many organizations using Azure AD only joined devices, especially as organizations move to more of a hybrid workforce. Many end users are finding they don’t need a VPN to access company data because they have everything they need in their cloud resources. Even if a device doesn’t have AD or traditional AD-join, you can still manage the compliance workstation to ensure it’s compliant and meeting requirements.
Beyond using the out-of-the-box configurations, you can create your own compliance check. For example, you can check for a specific application or file that you need to ensure it exists to enforce your policies. To do this, you can create a custom PowerShell script, upload it to Microsoft Intune, and report back to a JSON file to validate compliance, passed checks, and include any other specific information for the end user.
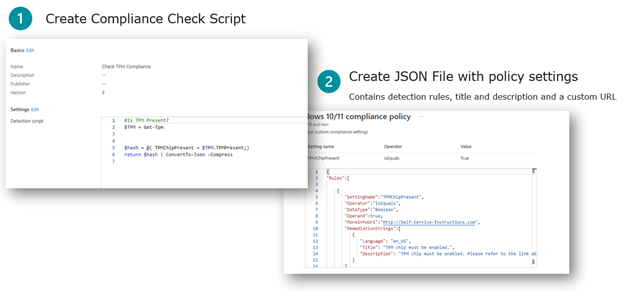
If you’re using Configuration Manager on-prem, you can also use configuration baselines built into the tool to report on compliance for co-managed devices.
Work with End Users to Remediate Gaps in Standards
Ensure that end users know what changes are coming, what they need to do to proactively get their devices into a compliant state, and who to contact with questions if they have any issues.
When you’re implementing and enforcing policies, make sure to follow the right steps to get your environment out in a compliant state. Prioritize training end users and clearly communicate when you will turn on the policies so users aren’t alarmed if they see messages and warnings. Also, work alongside the business to ensure they have correct information and know where to go if they have any issues.
Using our management tools, we can proactively know who’s out of compliance and contact them to fix it. We can also script remediation to simplify the experience for end users and even make it self-service through a Company Portal app they can run when they have time for a reboot.
Create Exception Scenarios
Sometimes devices might be too old to meet the hardware requirements and to allow remediation, so make sure you create exception scenarios. Build into your plan that it might be required to replace some devices. For replacement devices, ensure that applications and user data can be backed up and restored – and make sure you have spare devices available for this use.
Tool tip: Use Microsoft Intune to send templated emails to end users telling them that their device is out of compliance with corporate standards, how to get back into compliance, and how many days they have to remediate the issue.
Enforce Policies and Require Compliant Devices
Once you have remediated outstanding issues it is time to enforce policies that require compliant devices. When everything is in place, ensure that you enforce the policies and require compliant devices. To do so, use conditional access to disallow non-compliant devices from accessing any company resources (this requires that the device is enrolled in your management tool and that it passes the compliance check).
You can also set options for non-compliance like setting a grace period of # of days to remediate noncompliance. If issues aren’t resolved within the grace period, you can lock the device or retire it (which will unenroll it from your management system and erase all company data on the device).
Conclusion
As end users move between networks, devices, and working spaces, endpoint security has become more complex. But our secure workplace solutions help you protect your people and your data so you can support your hybrid workforce. And with 24/7 endpoint security monitoring via our managed services, you can be prepared for any disruption. Contact us to learn more about how to secure your hybrid workforce.
[Bonus] Appendix: Tools to Report, Manage, and Enforce Compliance
Microsoft Intune and Microsoft Configuration Manager are actually several different tools in one with autopilot provisioning, cloud-based management with Microsoft Intune, and on-premises management with Microsoft Configuration Manager (formerly known as System Center Configuration Manager). These tools can be used to collect inventory, perform patch management, deploy and update applications, manage security policy, set device configuration policies, and (of course) verify endpoint compliance.
Entra ID is your policy engine within the environment. It will define what you allow, detail your access requirements, and enforce device compliance before allowing access to the data.
Conditional Access is where we spend a lot of time with clients to help them determine exceptions like a Bring Your Own Device (BYOD) policy, what users can access, and what access should look like for a compliant device outside the environment. Those policies will drive your configuration standards.
Third-Party Integrations can also be used to manage device compliance. Some leading endpoint configuration products integrate directly with Azure AD and Conditional Access. One popular third-party integration is JAMF Pro for managing MacOS devices. It can integrate directly into Azure AD, allow for compliance to be set on those devices, and report on if they follow the standards you’ve set for them. This integration is very useful because many of our clients already have these technologies deployed, and they can use them to send a compliant / non-compliant signal to Azure AD to control access. Using third-party integrations also helps organizations avoid the costly and time-consuming process of having their workforce manually bring in their devices to be enrolled in a new tool.
This blog post was excerpted from Matt’s on-demand webinar, “Securing Your Hybrid Workforce: Effective Ways to Manage Window & Device Compliance.” Click the image below to watch his full presentation.




