Collaboration is a driving force in today’s organizations, but a lack of security can have a devastating and lasting impact. One click can result in a massive malware or ransomware incident and the loss of critical data. Workforce solutions must address the increased interconnectedness of internal teams, business partners, vendors, and customers to protect the sensitive data of all parties.
Microsoft Teams has emerged as the new virtual workspace for organizations with over 270 million users in 2022. It allows users to chat instead of send email, use multiple teams to collaborate, securely edit files with co-workers, take meeting notes, plan project tasks, conduct meetings, lead townhalls, host webinars, and much more. Using approved devices, employees can work from anywhere on Microsoft Team’s cloud-based app to connect and create in new ways.
Native Security in Teams
Microsoft Teams utilizes network communications that are encrypted by default. In fact, most of the security acronyms that come to mind when considering security standards for your organization are an innate part of Teams like:
- Transport Layer Security (TLS) / (MLS)
- Server to Server (S2S) OAUTH
- Public Key Infrastructure (PKI)
- Secure Real-Time Transport Protocol (SRTP)
All that native security is then wrapped up with Azure DDOS network protection in addition to the throttling of requests coming from the same endpoints, subnets, and federated entities. In business terms, this means that everything in Microsoft Teams is not only encrypted, but also wrapped in as many security layers as possible.
User Security in Teams
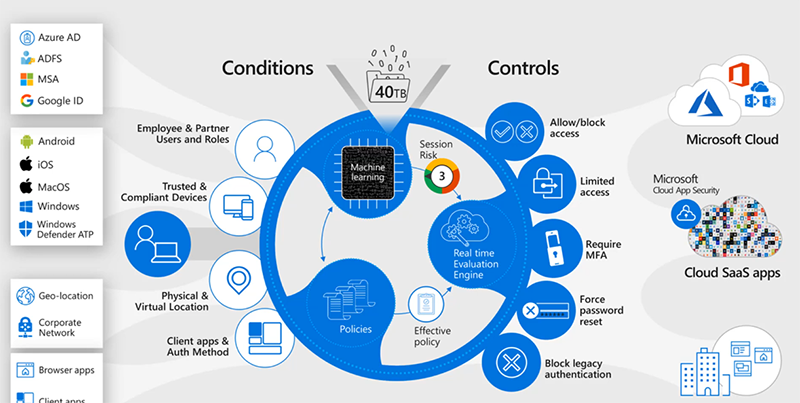
While you have that native security built into the Teams application, users can still pose a security risk. Microsoft (and Core BTS) recommends implementing best practices of Microsoft 365 Security Protection like multifactor authentication (MFA) and Identity Access Management (IAM) to reduce this risk. While the additional challenge of MFA may be considered inconvenient to users, the significant reduction in compromised user security makes it worthwhile.
Your entire Microsoft 365 tenant (including Microsoft Teams) can use Identity Access Management (IAM) and Multi Factor Authentication (MFA) protocols to ensure the right users have access to your data. If a malicious user obtains valid credentials and tries to access your system through an anonymous server, the suspicious IP address will be identified, and the user access blocked — keeping your data secure.
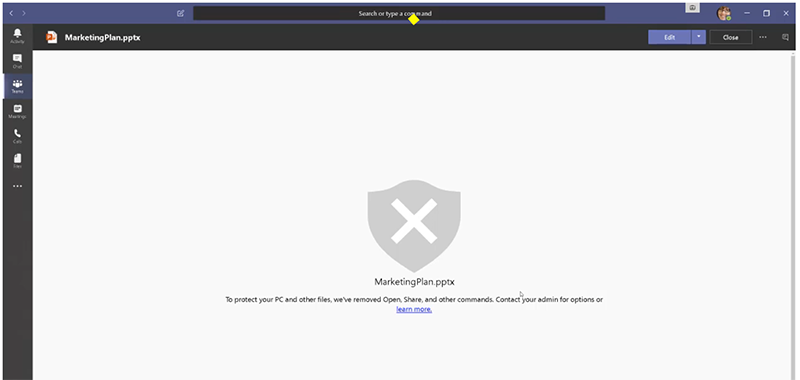
Advanced Threat Protection for File Security
Imagine that a vendor, who collaborates with your team, inadvertently uploads a file with malware into a team channel. If your employee opens the file, you’ll have a potential nightmare on your hands. With Microsoft’s Advanced Threat Protection (ATP) capabilities, the malware-infected file is immediately identified, quarantined, and monitored to prevent a malicious attack.
InTune Device Management
In today’s BYOD (Bring Your Own Device) culture, it is now possible for organizations to monitor each device used by employees and stakeholders when accessing Microsoft 365 content and applications. As part of a Zero-Trust architecture, Microsoft InTune can be associated with most user licenses beginning with F1 and F3 on up (including G3 and G5). When a user first logs into the Teams application, they are prompted to accept a Terms of Use agreement that includes installing the InTune Company Portal app.
As a company, you set the rules and policies to specify which data can be accessed through the app. If the device does not meet your criteria, or the authentication cannot be verified, no data will be sent to the device – preventing the user from accessing your data.
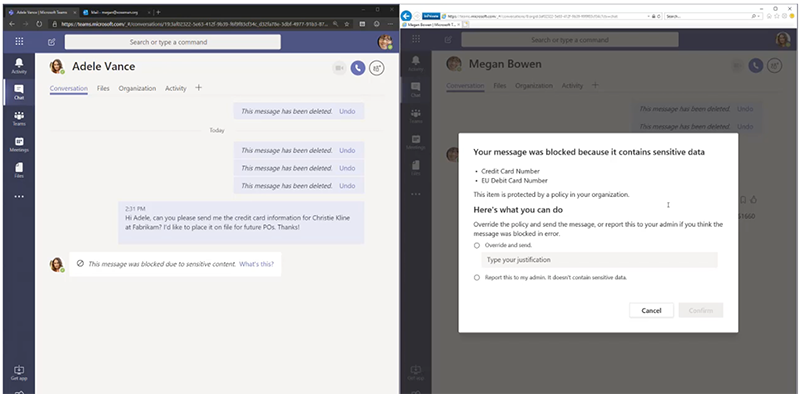
Data Loss Protection (DLP)
Your teams work hard and play hard. If one of your team members innocently distributes their AMEX number to the rest of the crew to go buy pizza, the Data Loss Protection feature will recognize the credit card number as sensitive information and alert the user to provide a justification before the message can be sent to the team. Without justification, the message won’t be sent, protecting not only company assets but also employee personal data. Other types of sensitive can also be identified, alerted, and prevented from distribution.
Securing External Access
Another threat often associated with Teams collaboration occurs when a guest user is allowed into your environment. This can be as a guest to a team or as a guest to a meeting. Securing the settings related to inviting guests to a team, how non-employees join meetings, and sharing documents with external people is critical to mitigate potential issues.
Some Teams security best practices include:
- Requiring guests to be invited to a team and registered using Azure B2B
- Prohibiting guests from deleting channels in a team
- Prohibiting sharing with anonymous users
- Allowing only members of the organization to automatically join a meeting (everyone else goes to the Lobby and must be admitted to the call)
- Requiring permissions for attendees to present content in a meeting as a default setting
These configuration settings can be applied to the global policy in the Teams Admin Center.
Limit App Availability
One of the greatest collaboration tools in Teams is the ability to add an app to a team or to access it directly in any user’s Teams client. Currently there are over 1,800 apps available to users in the Teams App store. However, only 43 of those are Microsoft-published apps. Although Microsoft provides testing and validation for all apps added to the Teams Apps store, limiting what is available in your tenant app store reduces confusion for users and reduces the load on administrators and your support desk.
The Teams App store allows your organization to build custom apps which can be made available to your users. It is a good practice to turn off the ability to allow the uploading of custom apps to Teams. Instead, create a custom policy to allow only those users who meet your organization’s security requirements the ability to upload custom apps.
Need More Teams Security?
Microsoft recently announced that Teams Premium licensing will be launched in December 2022. It will allow the addition of watermarks to content shared during meetings, enable a higher level of encryption on meeting recordings, the ability to designate who can record a meeting, and the application of sensitivity labels to automatically add meeting options.
In Summary
We have taken a high-level look at the main security features in and around Microsoft Teams, including:
- Teams App security uses the latest security protocols.
- Microsoft 365 Security Protection is a layer of additional protection around the Teams App and Microsoft InTune provides organization control of devices.
- Users are secured using MFA and IAM.
- Additional security requirements around external users and file/data sharing increases security.
- Configuration in the Teams Admin Center allows you to fine tune security for the day-to-day usage of the Teams App.
If you need more details on security or assistance, don’t hesitate to contact Core BTS.




