(This blog was excerpted from our Passwordless Authentication webinar that you can watch on-demand)
What is Passwordless Authentication?
As its name implies, Passwordless Authentication is a method of authentication that is not sending a user known password. Passwords are considered symmetric, meaning the plaintext value of a password a person knows is the same value stored in the application or authentication system. It’s typically hashed or encrypted. But passwordless is asymmetric. It uses public key cryptography, the same type of cryptography that secures the web via TLS. The use of public key cryptography replaces the exchanged secret between the end user and the authentication system.
Passwords are very convenient because they don’t require any special hardware or software to implement. However, they can easily become insecure once someone obtains them through social engineering tactics, phishing keyloggers, or other means. Then you have passwords and two factor authentication, which strengthen the application at the cost of inconveniencing the user. Passwordless gets rid of the password that can be disclosed while also removing the dependency of that password being used on the application and leveraging modern hardware to provide multifactor authentication.
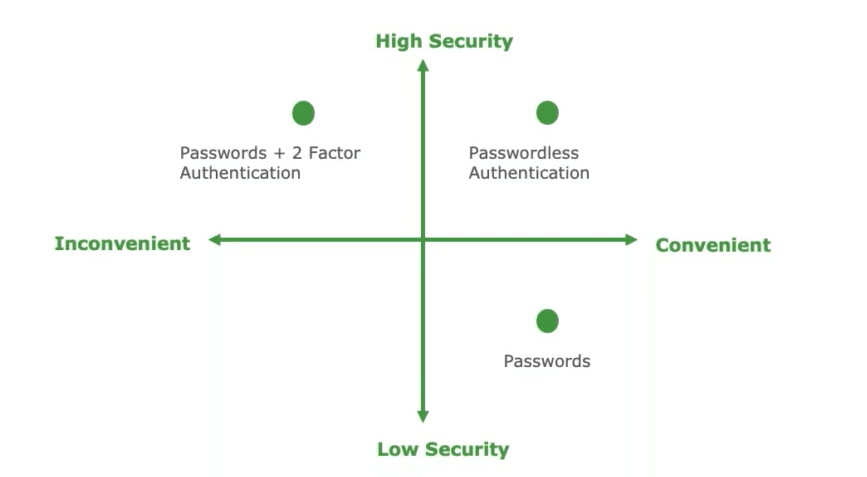
Why Explore Passwordless Authentication?
What have been the main drivers behind organizations auditing a passwordless architecture? It’s first important to understand the underlying security trends that are encouraging organizations to rethink how access is granted to critical information. One of the reports I like to use is Verizon’s annual data breach investigation report. An interesting statistic from the 2021 DBIR report is that roughly 61% of reported breaches involved credentials (though the stat also includes brute force attacks and insider privilege abuse). Also interesting is that 85% of breaches involved human interaction, meaning that hackers may have gained access through a social engineering campaign to acquire those credentials in the first place.
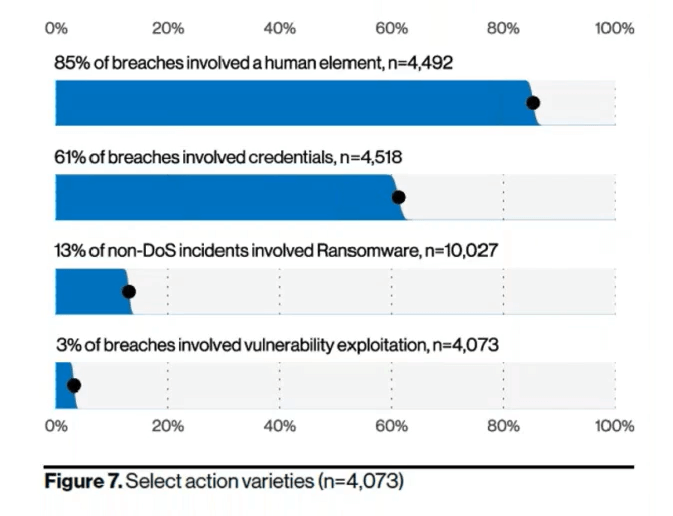
Many clients we speak with are frequently asking how to tackle ransomware threats, but it’s important to remember that ransomware typically requires hackers to gain access to the environment. Since many organizations feel they’ve installed the necessary prevention tools, it may be surprising to see how often hackers are bypassing those controls by simply walking through the front door.
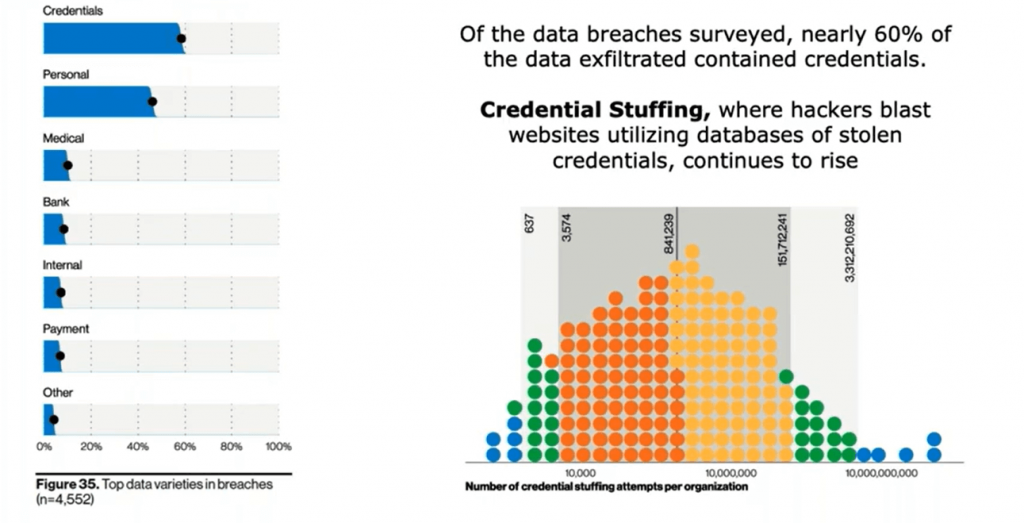
Credentials Remain a Hot Commodity
Once hackers are inside your environment, they are often stealing even more credentials. According to the Verizon report, credentials are stolen in breaches even more than personal information. Hackers then use these credentials to perform “credential stuffing” where they use the credentials in large “drive-by” campaigns to see where the credentials work elsewhere on the web. By combining credentials with the other information they gain (like personal information), hackers increase the likelihood they will find the right combination to successfully breach your environment.
Password Re-use Remains a Huge Problem
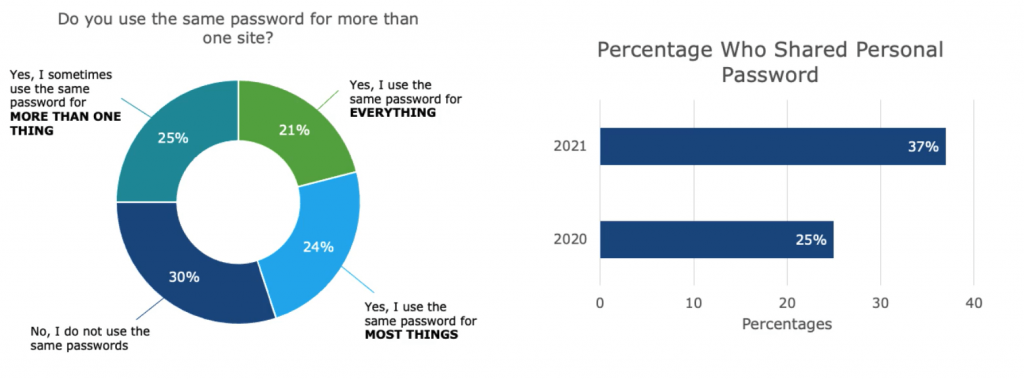
How many passwords do you use for your personal devices, personal accounts, streaming, etc.? In a recent poll, we asked professionals how many password-based credentials they currently maintain, and these were the results:
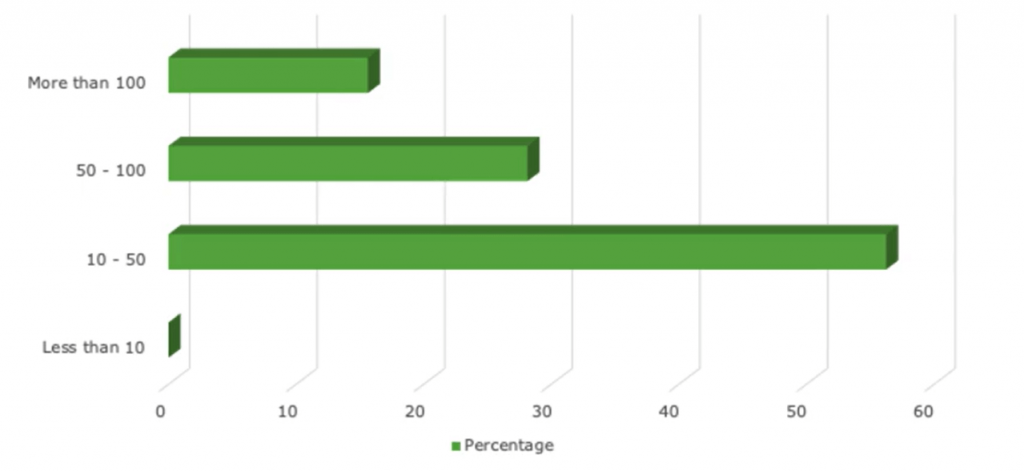
One of the reasons credential stuffing campaigns are so successful is because users frequently re-use passwords across multiple services because it’s hard to remember what password we used for what service (and that’s not even factoring in regular password changes!). And to make it worse, users often share their credentials with friends and family (ex. streaming service credentials) who may even re-share the same credentials with their network. This increases the possibility that credentials are stolen and used in a breach attempt.
Problems with Password-Based Authentication
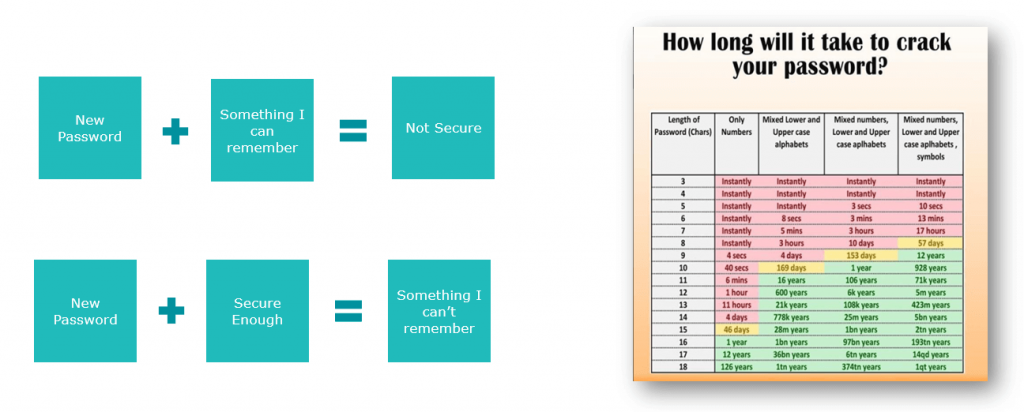
Given that one of the core tenets of security is confidentiality, it’s easy to see how security has degraded over time as passwords moved from something that you know to something that many people know. It’s difficult to solve this because passwords should be easy to remember; but if they are, then they also tend to be easier to brute force.
The table below demonstrates how long it would take for passwords to be brute forced, given certain complexities and password lengths. The challenge is that the more complex the password, the more difficult it is to remember, and the more likely the user is to re-use it elsewhere, which in turn makes it less secure. So how do we solve this problem?
Solving the Problem with Passwordless Authentication
With FIDO2 standards you can now shift to an MFA solution that is passwordless capable. You can even go usernameless for even more security, where the Identification is stored as a resident credential on the device or external hardware.
In this scenario, public key cryptography is used to exchange a signed-secret to an authentication system that can be verified using a public key. But essentially the “password” is uniquely paired to the site, identity provider, or authentication system. For example, if it’s a 2048-bit private key, then it would be equivalent to a 256-character password.
Pros:
- Convenient sign-on process for the user
- Passwordless authentication makes phishing less practical since it’s asymmetric
- Public key-cryptography used for authentication to system
- Each site\application has its own public key
- 2048-bit key pair = 256-character password
Cons:
- Broken hardware can make authentication difficult
- Applications or identity providers need to support the new API
- Need to have supported software, browsers
- WebAuthN and CTAPv2 is still relatively new for adoption
How to Move Forward with Passwordless Authentication
As you go passwordless, keep the following five items in mind:
- Create a process to handle lost or stolen devices: Make sure you have a process to handle lost or stolen devices, especially ones where biometric hardware has been damaged. Consider offering roaming FIDO2 compliant security keys as a means for recovery access
- Enroll in multiple forms of biometrics across multiple devices: If you have a biometric sensor, ensure your face and multiple fingers are enrolled with it for maximum redundancy.
- Be aware that you will have to co-exist with passwords until you’re truly passwordless: Be mindful of what your existing password is and whether or not it might have been disclosed because hackers might be able to leverage that to bypass an authentication system using the password vs passwordless.
- Consider the role of self-service password reset: SSPR is traditionally used to help recover access to an account where someone lost a password. Therefore, you will want to establish a similar support process to help a user recover access to a device and environment.
- Decide whether to use Windows Hello or Windows Hello for Business: If you have a personal device, Windows Hello can be used to help secure your local sign-in by obscuring your username and password with a Windows Hello form of authentication. For Enterprise organizations, it’s recommended to evaluate Windows Hello for Business deployment models such as Key-Trust, Certificate-Trust, or Cloud-Trust which eliminate passwords.
To learn more about how you can secure your environment, contact us to talk with our security experts.





